Learning GitHub from Basics (1) - A Linux Developer Pushes to My Repo?
How GitHub commits work
This post has been translated from Korean to English by Gemini CLI.
These contents are organized based on my curiosities and the very good articles on the Programmers blog.
- Git Command Collection for Beginners (1)
- Git Command Collection for Beginners (2)
- Git, GitHub Command Usage Tips
The reason for organizing is that I use GitHub in projects, and developers have no choice but to use GitHub, but I feel like I’m using it without knowing the principles properly + without knowing the commands or functions well.
Starting from Scratch
Configuration Files
Git can configure files by scope.
- system: System-wide configuration file -
/etc/gitconfigcan be specified - global: Current user (user logged into the shell) -
~/.gitconfigcan be specified - local: Current working repository -
.git/configcan be specified
These settings are loaded in the order of system -> global -> local. (That is, if there is a setting overridden in local, it is applied based on local)
Then, before committing, you need to set user.name and user.email. (You might have forgotten if it’s been a long time)
1
2
git config --local user.name pobi
git config --local user.email pobi@gmail.com
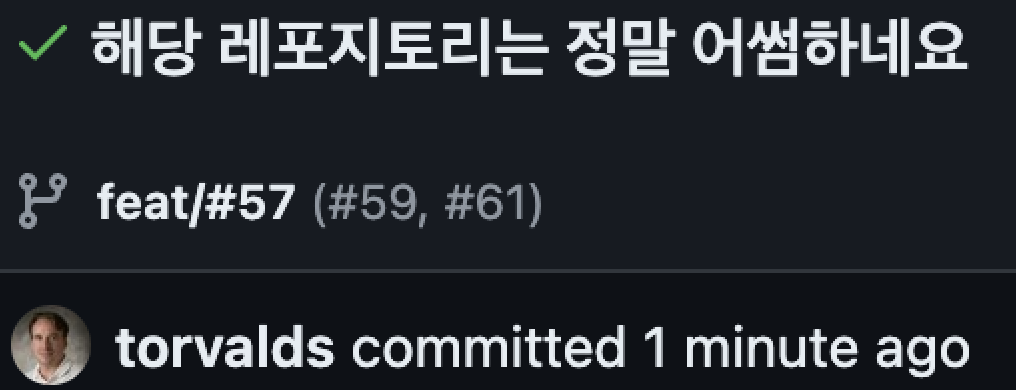
But what happens if you set it to a value that is not your email or name?
In this way, Push works completely.
Why? The name and email set in Git are simply signatures of who made the commit. They are not for authentication.
Therefore, when you Push, it is uploaded with that name and email.
Of course, it is possible to impersonate a famous person (above is the founder of Linux).
Then, you might think that it’s possible for someone to impersonate me or a celebrity. (Of course, when pushing to a remote repository, it operates based on SSH or PAT.)
To solve this uncertainty, GitHub has something called GPG.
GPG
GPG is an acronym for GNU Privacy Guard. Based on Mac,
1
brew install gnupg
Install with.
It ensures data confidentiality, integrity, and authentication through public key - encryption key. And it follows OpenPGP (standard for public key cryptography).
1
gpg --full-generate-key
If you start generating a key through,
1
2
3
4
5
6
7
8
Please select what kind of key you want:
(1) RSA and RSA
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(9) ECC (sign and encrypt) *default*
(10) ECC (sign only)
(14) Existing key from card
It asks for the encryption method like this.
1
2
3
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (3072) 4096
Requested keysize is 4096 bits
It asks for the key size.
1
2
3
4
5
Real name: pobi
Email address: i894@naver.com
Comment: "Test Key"
You selected this USER-ID:
"pobi ("Test Key") <i894@naver.com>"
It receives the real name, email, and comment as the user ID.
1
2
3
4
5
6
public and secret key created and signed.
pub rsa4096 2024-08-25 [SC]
2C072860295ADFD4E2A50D725366C23D85105AF9
uid pobi ("Test Key") <i894@naver.com>
sub rsa4096 2024-08-25 [E]
Then, a key is created based on this.
To put this key in Settings -> SSH and GPG keys,
1
gpg --armor --export pobi
Output the public key and copy and paste it. (At this time, you can export with any name, email, or comment.)
After that,
1
git commit -S
When committing, sign with the -S option. At this time, the signature automatically retrieves the encryption key based on user.email and signs.
Then, the signed commit will be uploaded to GitHub!
With what I’ve thought so far, You might think, “Isn’t it the same if I create it with someone else’s name and email and register the key?” That’s normal. I did too.
However,  If it’s not an email authenticated in your account,
If it’s not an email authenticated in your account, Unverified appears like this.
 In this way, it is authenticated only when there is a GPG Key for the email I have authenticated.
In this way, it is authenticated only when there is a GPG Key for the email I have authenticated.
Conclusion
Unverified and commits with no value are untrusted commits. Someone could maliciously impersonate and commit.
However, it would be too annoying not to trust all of this, right…? In a project, it seems okay to go with trust-based without unnecessary suspicion.
1
git config --global commit.gpgSign true
To automatically sign all commits, turn on this option.